In this blog , I will explain what all configurations we need to perform to establish a federated SSO between IDCS which will act as IdP and Oracle Fusion - SaaS which will act as Service Provider - SP
Pre - Configurations :
- IDCS :
- Get the Oracle IDCS - IDP Metadata XML using this link: https://<IDCS-Service-Instance>.identity.oraclecloud.com/fed/v1/metadata
- Save the file - IDP_Metadata.xml
- Note: In case if you get an error like Page Not Working then follow the below instructions to enable certificate access.
- Login to IDCS admin console.
- Go to Settings
- Select Default Settings option
- Enable - "Access Signing Certificate"
- Save the changes.
- Now access the metadata URL.
- Fusion-SaaS:
- Get Service Provider Meta Data.
- Use the following URL and download the SP_MetaData.xml
- https://login-ics-dev1-saasfaprod1.fa.ocs.oraclecloud.com/fed/sp/metadata
- domain_name : ics-dev1
- Get Tenant and Domain Names:
- Example Fusion URL - https://fa-ics-dev1-saasfaprod1.fa.ocs.oraclecloud.com/fscmUI/
- Tenant or POD Name : ics-dev1
- Domain Name : saasfaprod1.fa.ocs.oraclecloud.com
Main Configurations:
Fusion-SaaS:
- Login to SaaS application using Security Admin User.
- Go to Security Console
- Select Single Sign-On on left Menu
- Click + Create Identity Provider.
- Select Edit On Top
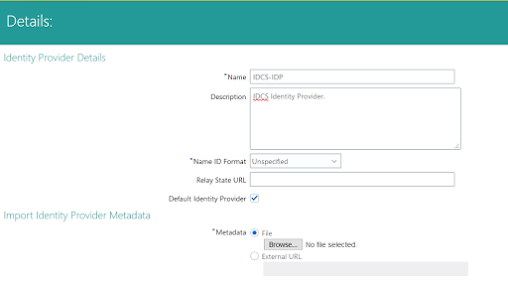
- Provide following details.
- Name : IDCS-IDP
- Description : IDCS Identity Provider.
- Name Id Format - Unspecified - Select from drop down.
- Select Default Identifier Option.
- Upload the Meta data file downloaded from IDCS - Refer Above Pre-config steps.
- Save and Close
- Select Service Provider Tab
- Download the Service Provider Signing Certificate.
IDCS Configurations:
- Create Fusion Application :
- Login to IDCS
- Go to Applications
- Select Add ( + )
- Select App Catalog
- Search for Oracle Fusion
- Select R13 app
- Provide following details to the App -
- Name : Fusion ERP SSO App
- Description : Fusion ERP SSO App
- Select required SaaS Applications
- Go to Next Page
- Open the SP_Metadata.xml file downloaded as part of pre-config step.
- Get EntityId value
- entityID="https://login-ics-dev1-saasfaprod1.fa.ocs.oraclecloud.com:443/oam/fed"
- Assertion Consumer Value:
- <md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://login-ics-dev1-saasfaprod1.fa.ocs.oraclecloud.com/oam/server/fed/sp/sso" index="1"/>
- Upload the signing certificate that was downloaded from Fusion apps during SSO configuration. Refer Above Fusion activity .
- Download Signing Certificate and Identity Provider Metadata and save as file and click “Next”
- On the Provisioning tab DO NOT Enable Provisioning and click the Finish button to complete the application setup
- Activate the application.
TEST and ENABLE SSO :
- Login to SaaS application using Security Admin User.
- Make sure the user is present in IDCS and updated as Federated. Same User is present in SaaS as well --- Note
- Go to Security Console
- Select Single Sign-On on left Menu
- Select the IDCS-IDP created earlier.
- Select Diagnostics and Activation
- Select TEST
- Select IDCS-IDP and Click Start SSO
- It will take you to IDCS login Page.
- Provide SSO credentials.
- After Successful authentication Status will get updated as Success.
- Enable Identity Provider.






No comments:
Post a Comment