Oracle offers multiple API management tools. API Platform Cloud Service and Oracle Native Gateway or OCI Gateway are the prominent ones.
API Platform Cloud Service will be managed by customers. Customer is responsible for managing API security and Infrastructure. Customer needs to provision API PCS and then provision gateway server (Weblogic Server) to deploy all the application API.
API PCS provides a management console to create and manage APIs . API's will be published to gateway servers. Gateway servers will connect and poll the changes and deploy them on to the server.
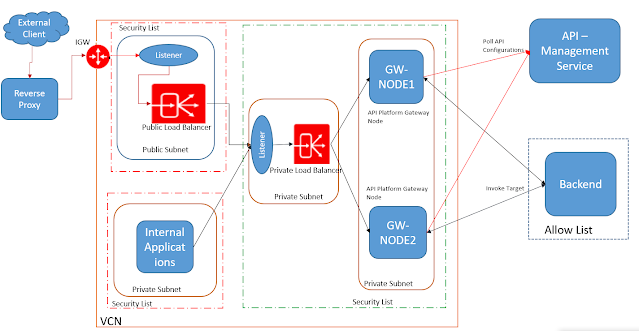
Following network flow diagram will show how the traffic flow can be configured and how the gateway servers will interact with management servers and backend applications.
API PCS
Oracle offers Gateway - a fully managed service to manage APIs. Here the customer is responsible for creating and managing API definition and security. Underlying infrastructure is managed by Oracle.
As part of OCI gateway configurations, we need to create a gateway and then deployments (API definitions). Gateway will be created on a specific Compartment , VCN and Subnet.
Specific security groups can be added or can be used to control access to the gateway. We can use custom certificates while creating a gateway to enable mTLS connection.
Create a deployment/API
- Provide a name. -- xxapi
- Provide a path prefix -- ogw
- Select create from Scratch Option
- Select Authentication Policy to restrict access using JWT or Custom Authentication.
- JWT
- Authentication Token - Header
- Header Name - Authorization
- Authentication Schema -- Bearer
- Issuer - https://identity.oraclecloud.com/
- Audience - Add the scopes to be allowed.
- Public Keys
- In this example , we will use the static key
- Static Key
- Provide a Key Id
- Format - JSON Web Key
- Get the Json Webkey from IDCS. Use the following endpoint to get the key - https://idcs-.identity.oraclecloud.com/admin/v1/SigningCert/jwk
- Remote JWKS : To retrieve the keys at run time.
- Create Routes
- Provide the incoming path
- Sample :
- /target/services/default/{contextRoot}/{client_ep*}
- Select the methods to be allowed from Source.
- Select the backend Type
- HTTP
- Oracle Function
- Incase of HTTP backend provide the backend URL
- https:/target_hostname/target/services/default/${request.path[contextRoot]}/${request.path[client_ep]}
- Can define multiple routes pointing to multiple target applications.
- Save changes.
OCI Command :
oci api-gateway deployment create --compartment-id ocid1.compartment.oc1..id_value --display-name dvpc2s --gateway-id ocid1.apigateway.oc1.eu-frankfurt-1.oci_id --path-prefix /dvpc2s --specification file:////home/VijayaKuma/tlndvpc2s.json

No comments:
Post a Comment